Introduction
OpenWrt is a highly extensible GNU/Linux distribution targeting wireless routers and is built from the ground up to be a full-featured, easily modifiable operating system for routers. On Sunlight the OpenWrt could be running as a very lightweight VM and connected to the software-defined networks in the Sunlight stack to serve as router and firewall. If a WiFi module is attached to the physical server running Sunlight, the OpenWrt VM could be also running as a fully-loaded wireless access point or client depending on the use case. In this article we will demonstrate the setup and configuration of OpenWrt as a firewall solution on Sunlight.
Network Architecture of Use Case
The typical use cases of the firewall are having a firewall in place between different networks, which could be either an internal network or external network. In this article we will use the firewall placement between an external network and two internal networks as an example to demonstrate the deployment of OpenWrt firewall on Sunlight.

Create the Networks
-
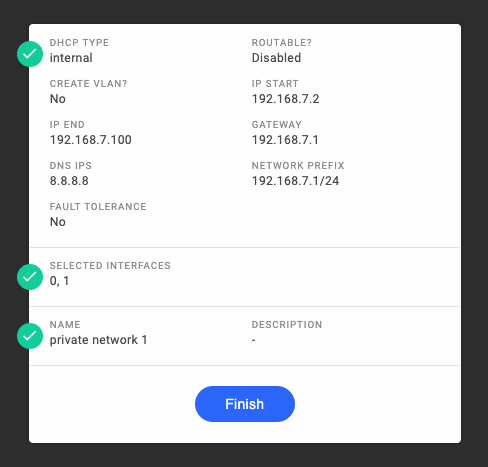
Create the private networks with the following options.
- Internal DHCP server
- Not routable
-
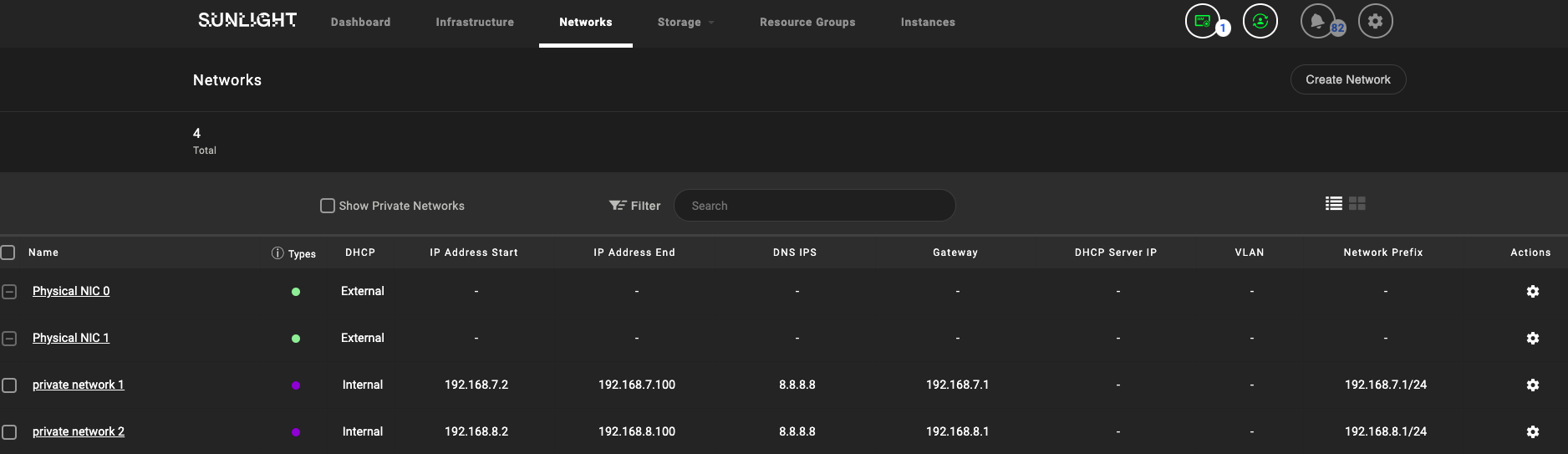
The "Physical NIC 0" in this cluster would be the external network.
-
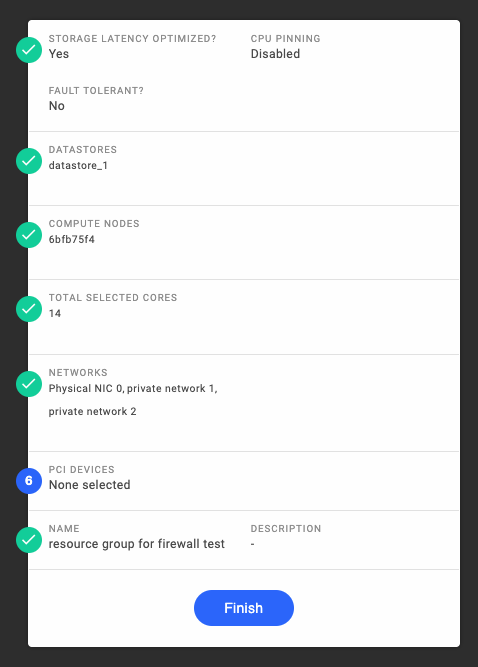
Add the networks into the resource group where the workload VMs are deployed.
Deploy the OpenWrt Firewall Instance
-
Add the template repository consisting of the OpenWrt image to the Sunlight cluster.
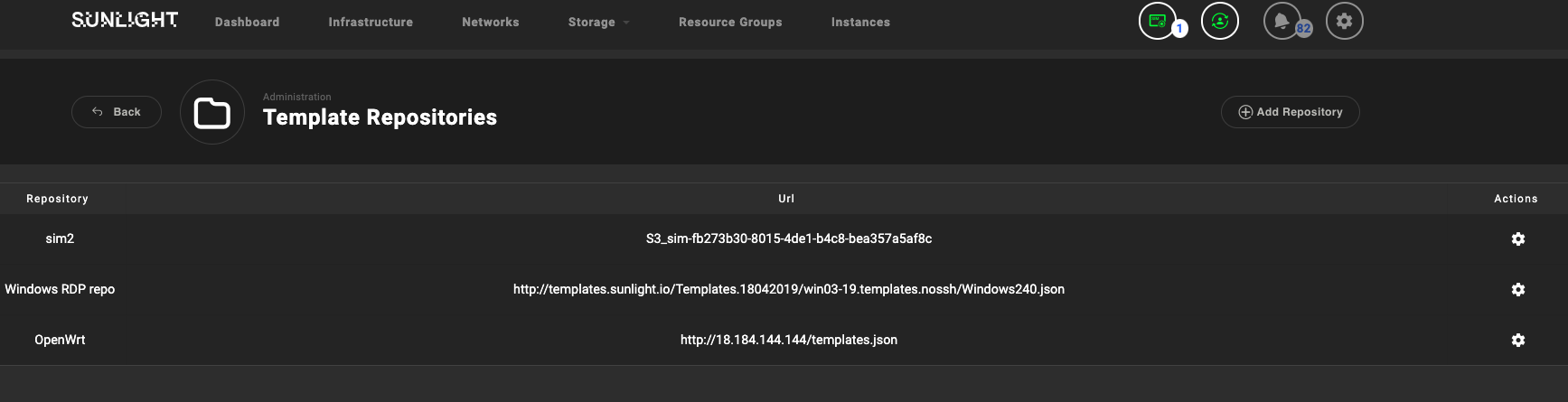
-
Download the OpenWrt image to the Sunlight cluster.
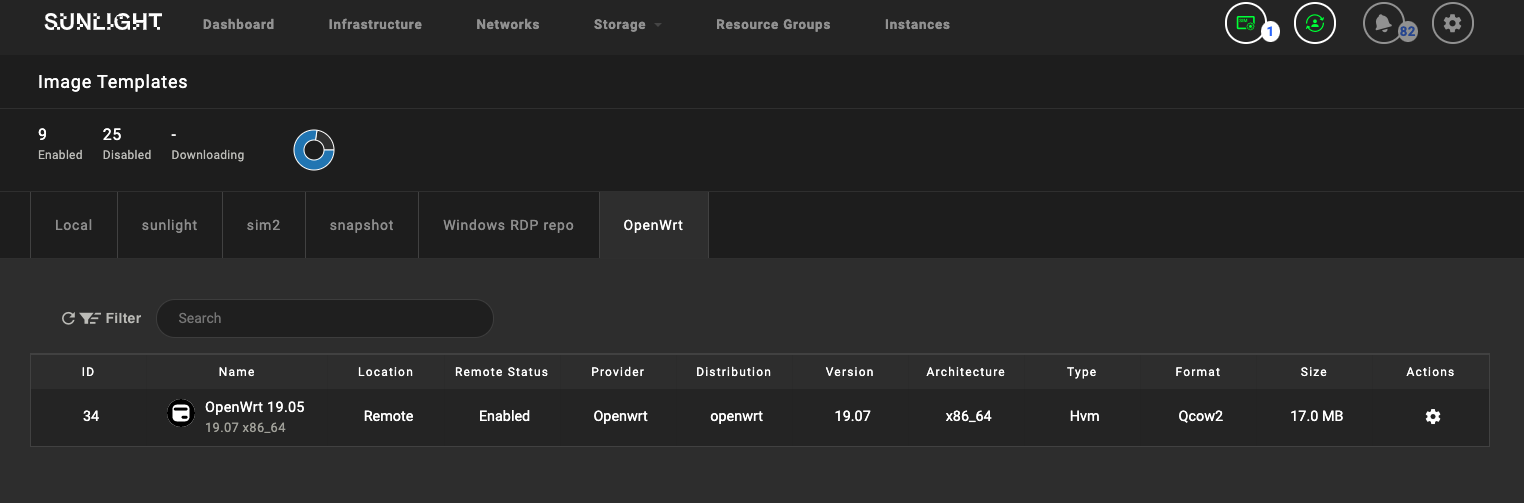
-
Create an OpenWrt firewall VM instance.
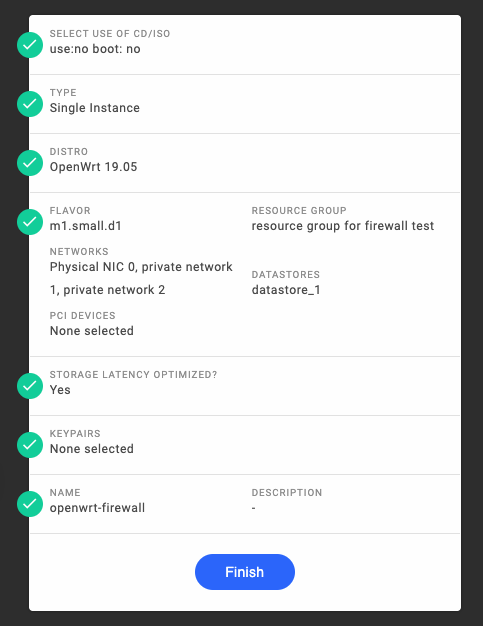
Configure the OpenWrt Firewall
-
Access the console of the OpenWrt instance.
For more information about the command line interface, please refer to the guidance provided by OpenWrt (https://openwrt.org/docs/guide-user/base-system/user.beginner.cli).
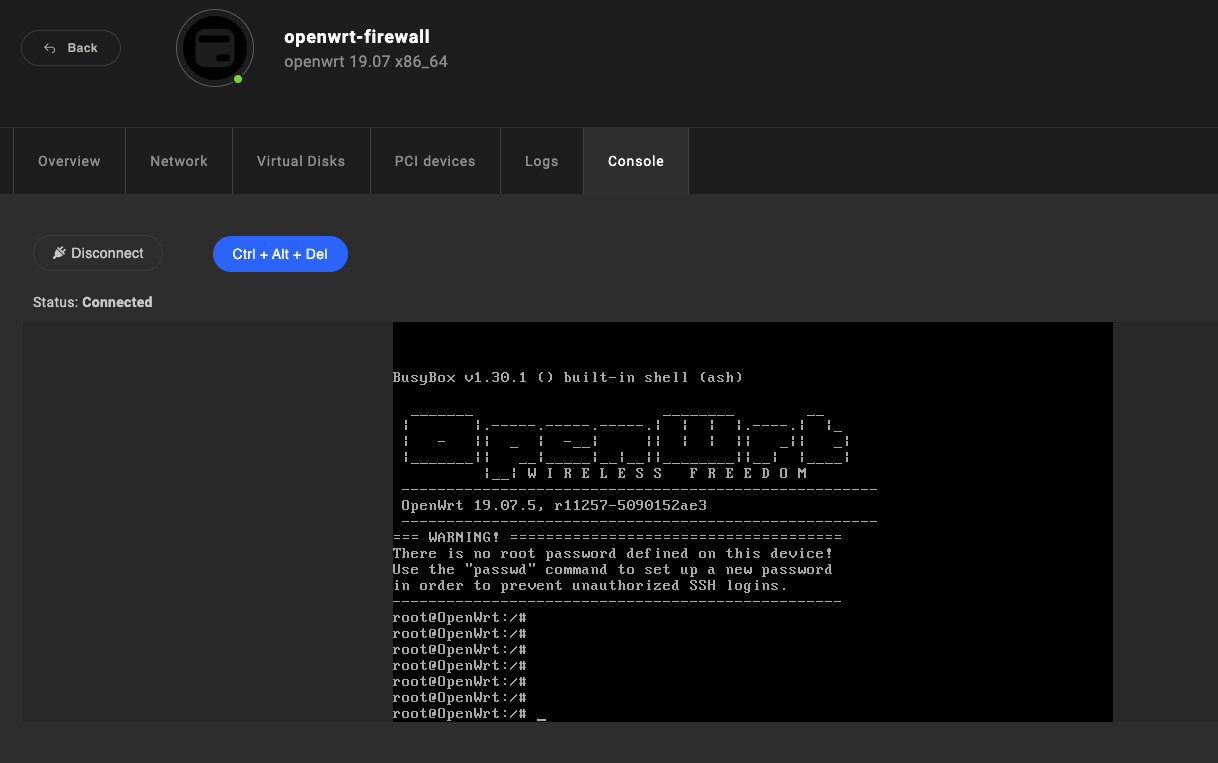
-
Access the dashboard of OpenWrt firewall. The default settings would allow the user to access the dashboard from the network in the LAN zone.
For more information about the dashboard configuration, please refer to the guidance provided by OpenWrt (https://openwrt.org/docs/guide-user/luci/start).
-
Configure the networks attached to the OpenWrt firewall instance to be the correct interfaces under OpenWrt configuration.
For more information about the network interface configuration, please refer to the guidance provided by OpenWrt (https://openwrt.org/docs/guide-user/base-system/basic-networking).
In the scenarios illustrated in this article, the network interfaces are configured as follows:
-
Network “Physical NIC 0” -- NIC “eth0” in OpenWrt instance -- “wan” interface
-
Network “private network 1” -- NIC “eth1” in OpenWrt instance -- “lan1” interface
-
Network “private network 2” -- NIC “eth2” in OpenWrt instance -- “lan2” interface
Edit the file /etc/config/network
config interface 'lan1' option ifname 'eth1' option proto 'dhcp' config interface 'lan2' option ifname 'eth2' option proto 'dhcp' config interface 'wan' option ifname 'eth0' option proto 'dhcp'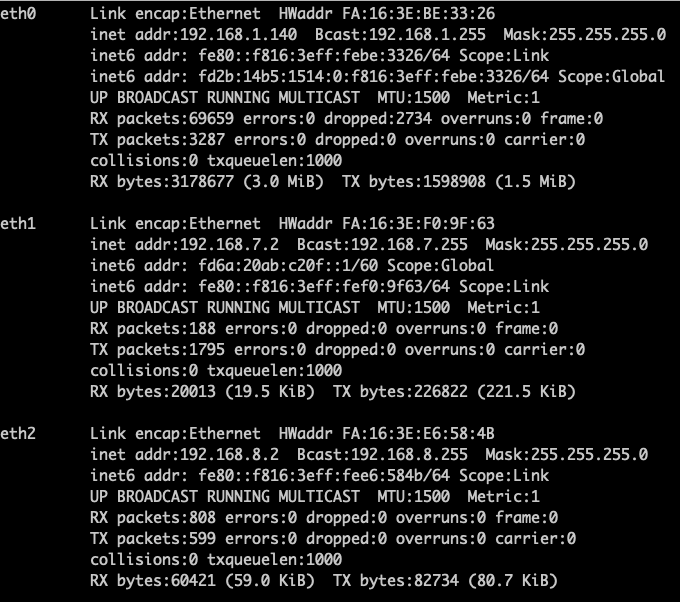
-
-
Configure the interfaces in the OpenWrt firewall instance to be within the desired network zones for firewall purpose.
In the scenarios illustrated in this article, the network "private network 1" and "private network 2" can access the "Physical NIC 0", so the basic firewall configurations are as follows.
Edit the file /etc/config/firewall
config zone option name lan list network 'lan1' list network 'lan2' option input ACCEPT option output ACCEPT option forward ACCEPT config zone option name wan list network 'wan' list network 'wan6' option input REJECT option output ACCEPT option forward REJECT option masq 1 option mtu\_fix 1 config forwarding option src lan option dest wan -
Configure more advanced firewall rules from the OpenWrt dashboard.
For additional information on Firewall configuration, please refer to the guidance provided by OpenWrt (https://openwrt.org/docs/guide-user/firewall/start).
Configure the Instances behind the Firewall
-
For the instances attached to the internal networks, since these networks are created with the option none-routable, there is not any network gateway created by Sunlight. When these instances are created by default they cannot access any other network.
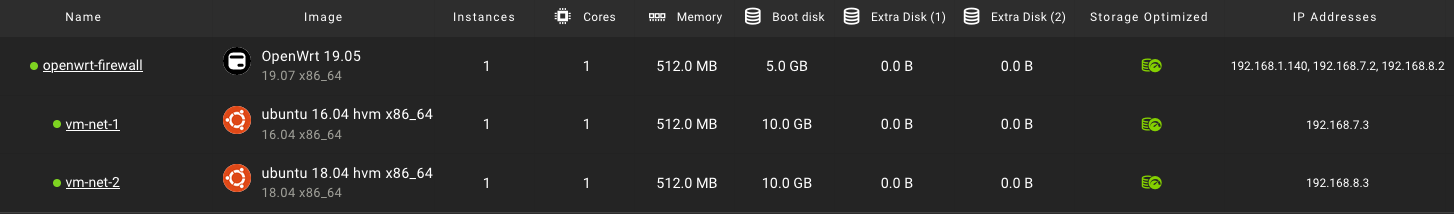
-
Since the OpenWrt instance is connected to both the external network and the internal networks, with appropriate firewall zones and rules configured as above, the OpenWrt instance can serve the instances as the gateway and firewall.
The basic rules configured in step 4 would allow the following:
- The networks in the "lan" zone would be able to reach each other.
- The traffic from networks in the "lan" zone would be forwarded to the network in the "wan" zone, and eventually to the Internet.
-
Configure the instances to use the interface of OpenWrt instance in the same network as the default gateway.
For example, for the instance "vm-net-1" attached to "private network 1", the default gateway of it would be configured as the OpenWrt instance's interface attached to the same network.
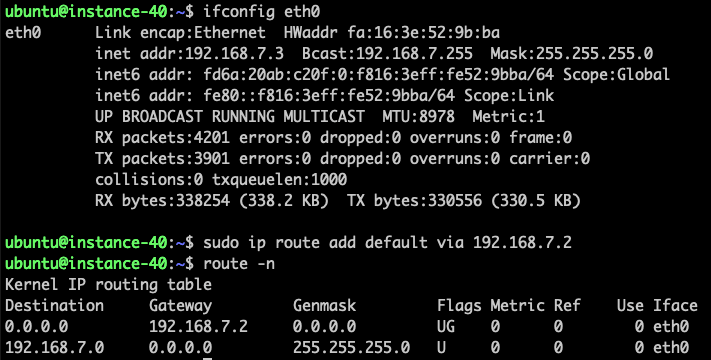
-
With the OpenWrt instance configured as the default gateway of the instances, the traffic from the instances would follow the rules listed in step 2 above.
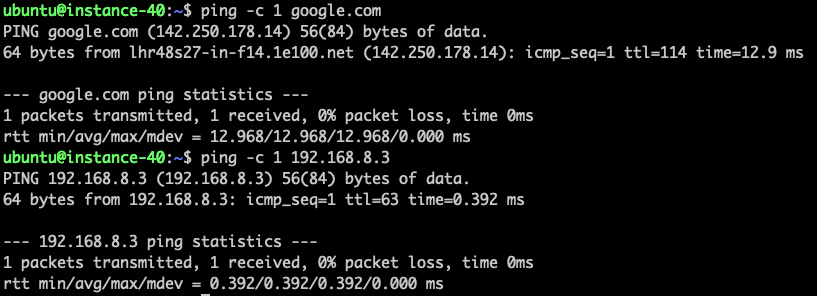
As an example below, the instance attached to "private network 1" would be able to access the Internet via the OpenWrt instance as gateway, along with all the firewall rules applied. Similarly, the instance attached to "private network 1" would be able to access the instance attached to "private network 2", where the OpenWrt instance serves as a L3 router.